Most industrial management systems do not have integrated security and are sensitive to any changes. At the same time, the scope of the attack on the cyber-physical assets is expanding, mainly due to the initiatives for digital transformation that stimulate the convergence of the networks of informational (IT) and operating technologies (OT). The entry of new technologies, like 5G, IoT and cloud services, is also increasing. More and more employees and external partners have more requirements for remote access, and this results in additional risks. The owners of factories and machine equipment depend on OEM manufacturers and the system integrators, thus exposing the crucial systems to additional risks.
What does an operating technology mean? The term evolves for the last few years as the most modern definition is “cyber-physical systems used for control, monitoring and optimization of physical processes, such as manufacturing of various products and management of the relevant infrastructure “.
The risk for the production networks (OT networks) is a proportionate to the connectivity. With the implementation of Industry 4.0 and the inevitable connectivity caused by the introduction of the Internet of Things (IoT) and the Industrial Internet of Things (IIoT), the possible access points for attacks also increase.
„Where is the problem? The core of the OT are the industrial control systems (ICS), where the so-called programmable logic controllers (PLC) are located, which by their nature are quite insecure. Most of the controllers do not have Zero Trust approach, and more often rely on the Assumed Trust philosophy. Meaning that if a message (request/ command) is formatted in the relevant language and is with the right protocol, the controller will simply perform it”, explain the experts of Kontrax.
According to Gartner, the factories and their equipment (OT environments) are traditionally isolated from external influence. However, with the technologies development and the modernization of the production, a need arises for connections to the business systems, OEM suppliers and other third parties. 15% of the interviewed under the research of Gartner, have experienced an incident in the field of security that had damaged a production or crucial equipment.
FUNCTIONAL DOMAINS OF IIOT, MAPPED TO THE THREE-LAYER TECHNOLOGICAL ARCHITECTURE
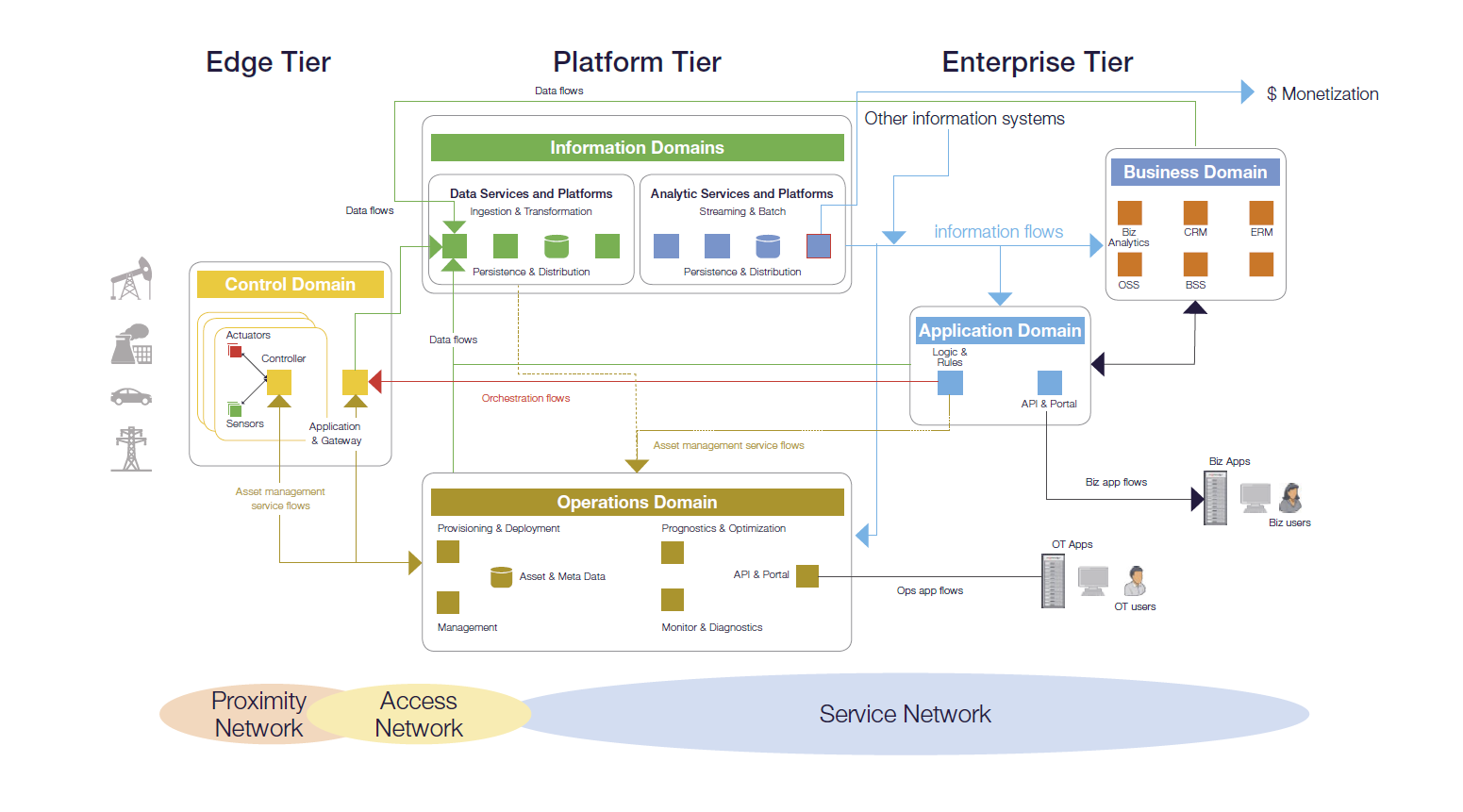
The automation systems are designed for safety operation, but rarely for being sustainable to cyber threats. On the other side, the operating technologies have a much longer operational life, as the automated hardware can operate for 20, even 30 years.
The participants in another research by SANS, year 2022, mention that the compromising of the IT equipment allows the penetration of malicious software in the control networks of the operating technologies, as the threat vectors of highest rank are towards the control systems.
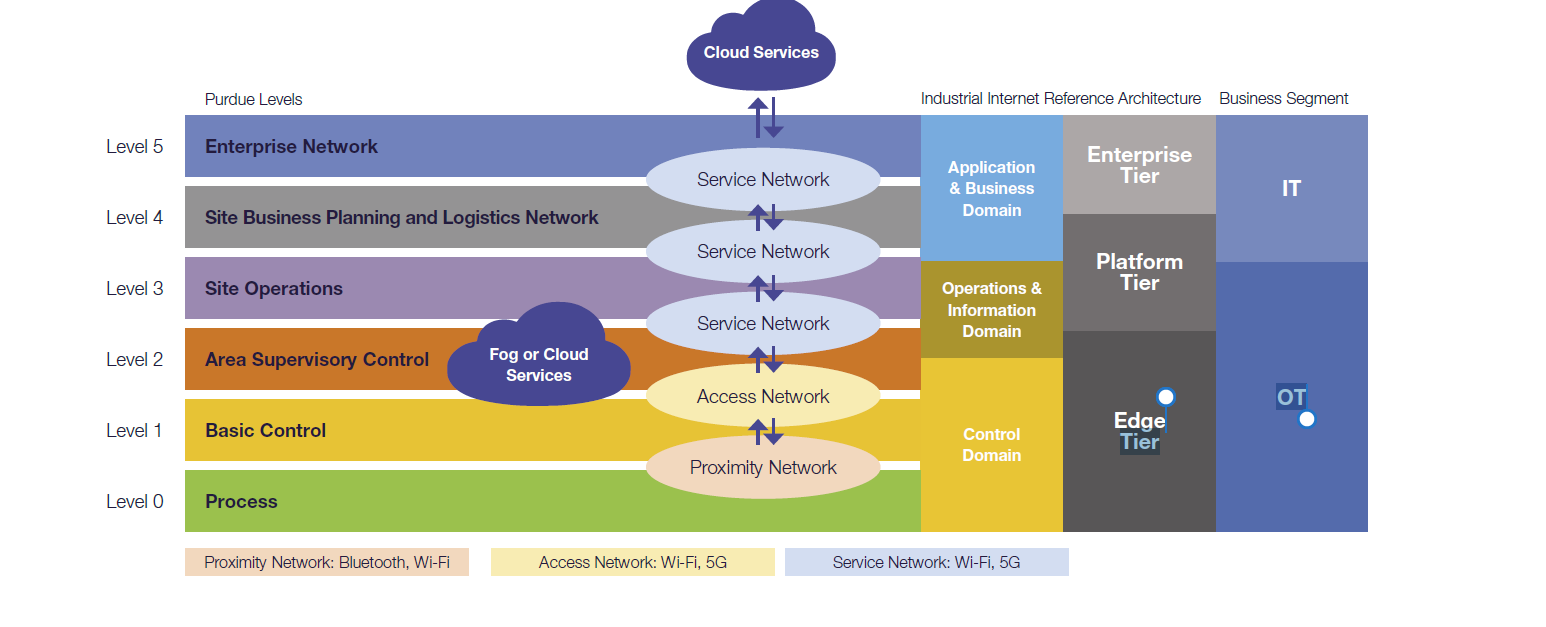
FUNCTIONAL DOMAINS OF IIOT, TECHNOLOGICAL LEVELS
This due also to the combination of the inherited and often outdated equipment, with the modern technologies. The technical integration of the inherited and outdated OT technology with modern IT systems is a great challenge for the good protection of the operating technologies and processes. The crypto-viruses (Ransomware), blackmailing or other financially motivated crimes, are number one vector of threat, which causes troubles for the industrial users.
The attacks against the OT infrastructure are more dangerous each day and have bigger consequences. In 2014 the medicine infusion pumps of a hospital were hacked, and in 2019 the factory of a global aluminium producer was stopped by a crypto virus. In 2021 the penetration in the systems of Colonial Pipeline became well known, and in 2022 there were more successful attacks on the production sector. Attack against Kojima Industries, supplier of car parts for Toyota, stopped 28 production lines, and hackers succeeded to block large part of the energy infrastructure of Ukraine.
THE SOLUTION – A COMPREHENSIVE APPROACH
Kontrax, as a partner of Fortinet, chooses the approach of the American supplier, providing an entire solution for protection of the operating technologies. It includes protected connectivity, as the digital transformation required protected sharing of data from the equipment to the data centres and the cloud. The remote access, providing smooth operation of the technicians and external partners on the maintenance of machines, also has to the protected. At the same time, the management of the OT and IT networks is provided as a synergy in united convergent control centre (SOC). They are supported also by the security services based on artificial intelligence, which allows the industrial control system to keep in line with the new threats.
According to an information from a report by Fortinet on the risks for the operating technologies, 9 of 10 OT organizations have already faced at least one penetration in their system during the last year, and 78% have had 3 or more penetrations, which is much higher in comparison to the data from 2021. For most of them the damages are related to loss of crucial data or intellectual property, damage on company image, even interruption of the operating technology, which endangered the physical safety of the employees. Very significant damage now is also the non-compliance with the legal requirements, which results in penalties or sanctions, as well as violations of the industry standards, thus losing market share and presence.
WHICH ARE THE IMPORTANT CONTROLS FOR THE PROTECTION OF/ AGAINST THE MEDIA
|
Segmenting and areas |
Segmenting protects OT against errors and hackers |
|
Secure remote access |
Activation of secure access for employees and thrid parties, who connect to the OT environment |
|
All levels visibility |
Something that is not seen, cannot be protected |
|
Access as per the role |
Restrictign thr access only for those who really need it |
|
End points protection |
Applying protection of the end point of the servers in or close to the protected peremeter |
|
Operating centers (NOC/SOC) |
Synergic advantages of all in one place management |
|
APT |
The advanced permanent threats (APT) require advance solutions. |
The solution - Security Fabric by Fortinet, implemented by the experts of Kontrax, provides unique convergent IT/OT/IIoT framework for cyber security for the owners of factory lines, helping them to reduce the risks, the weight of security on the OT teams. It ensures the interrupted operation and safety standards, as well as meeting the best practices and OT & IT regulations.
Amongst the clients, for which Kontrax have implemented the Fortinet solutions, are a leading company in the agricultural industry, an international company in the field of metal working, a leader in the aluminium extrusion and production of aluminium goods, pharmaceutical company and one of the biggest factories for production of synthetic soda ash in the world.

